Setup Okta with SAML
This walkthrough will go through an example of setting up Okta as an SSO provider for Argo CD (through the GreenOps UI).
You can view the Argo CD guide to configure Dex with SAML here.
Configuring SSO through the GreenOps UI
Okta Configuration
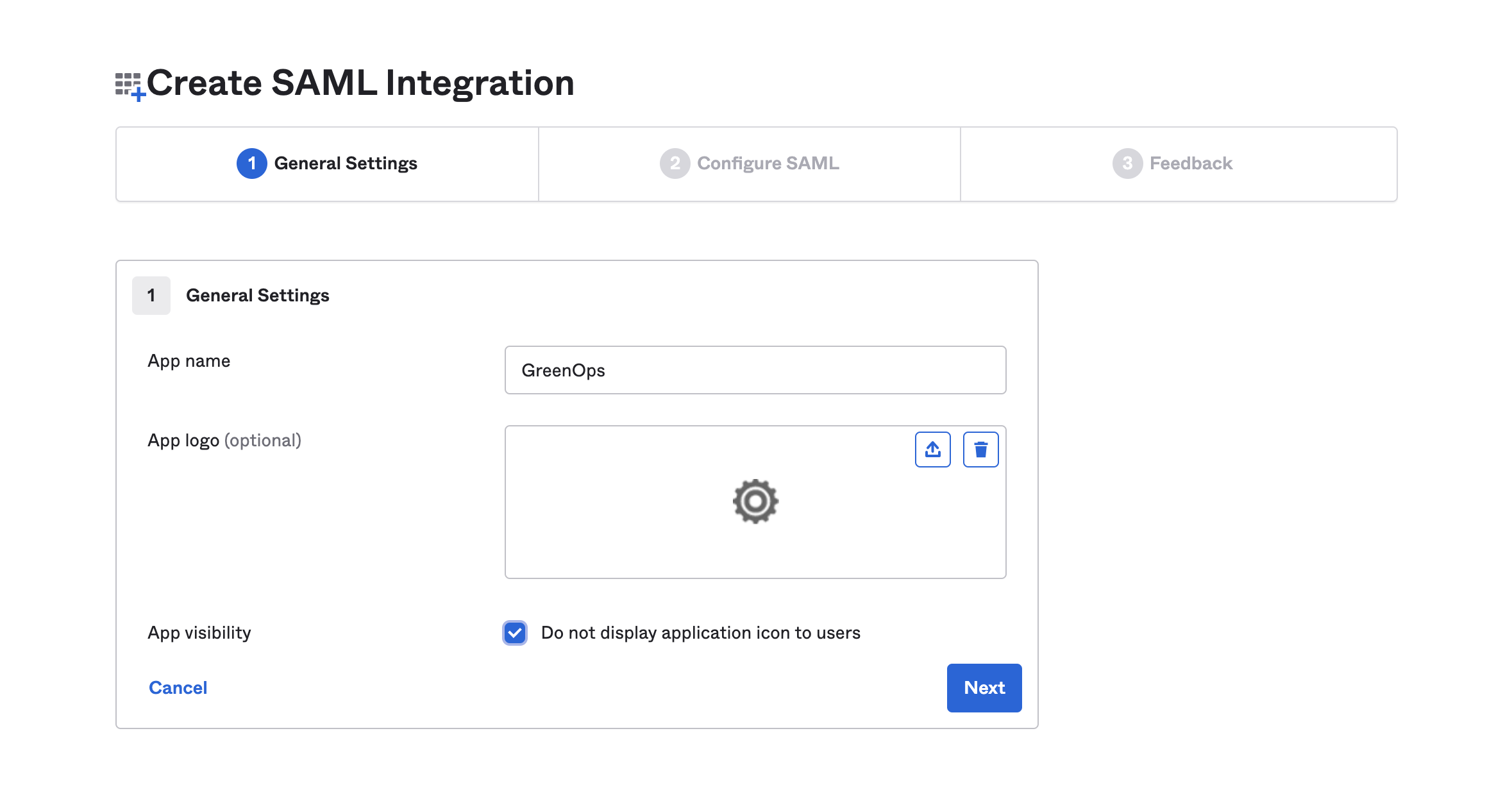
- In Okta, create a new SAML application:
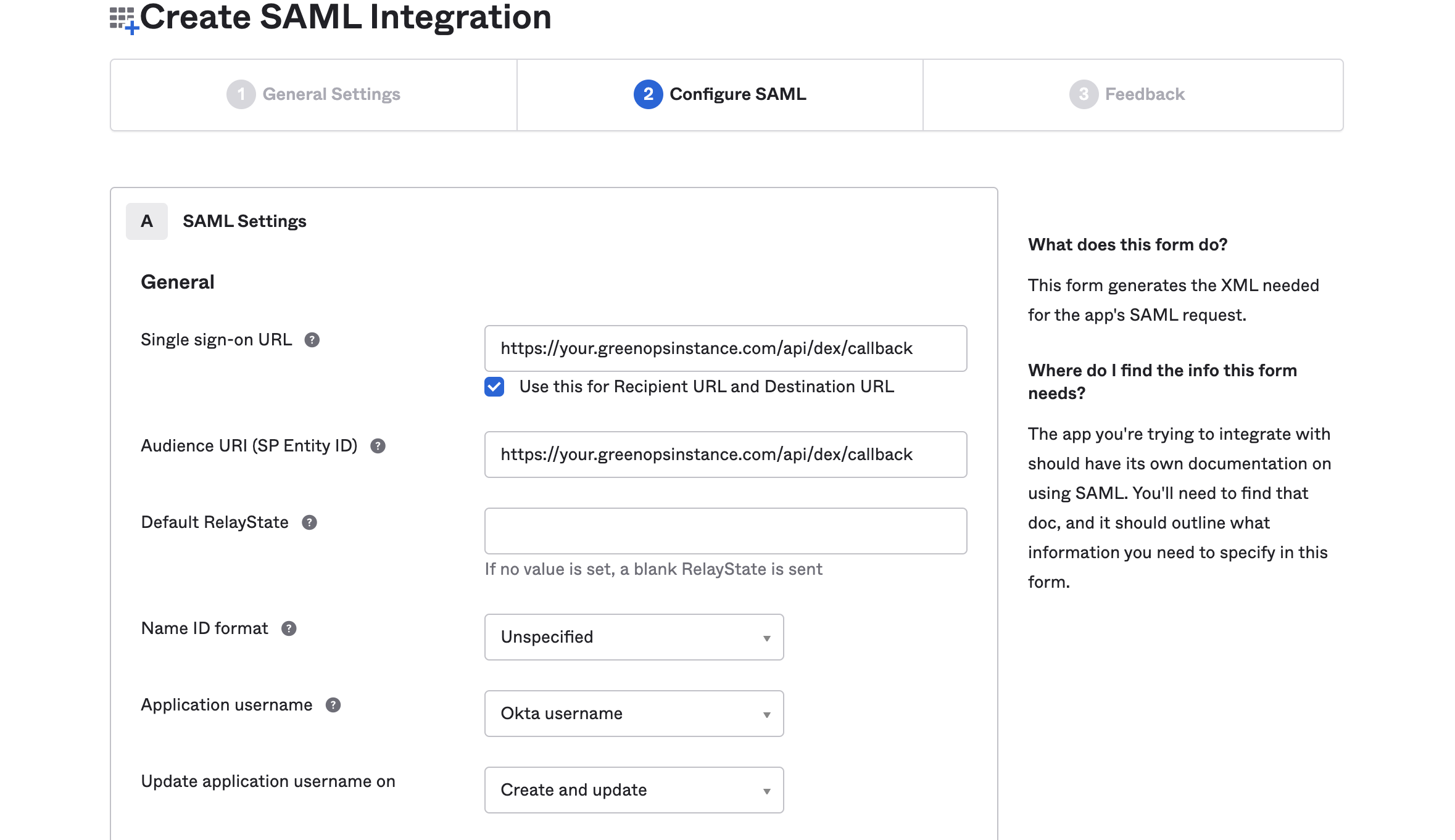
- Set up the SSO, callbacks, and groups:
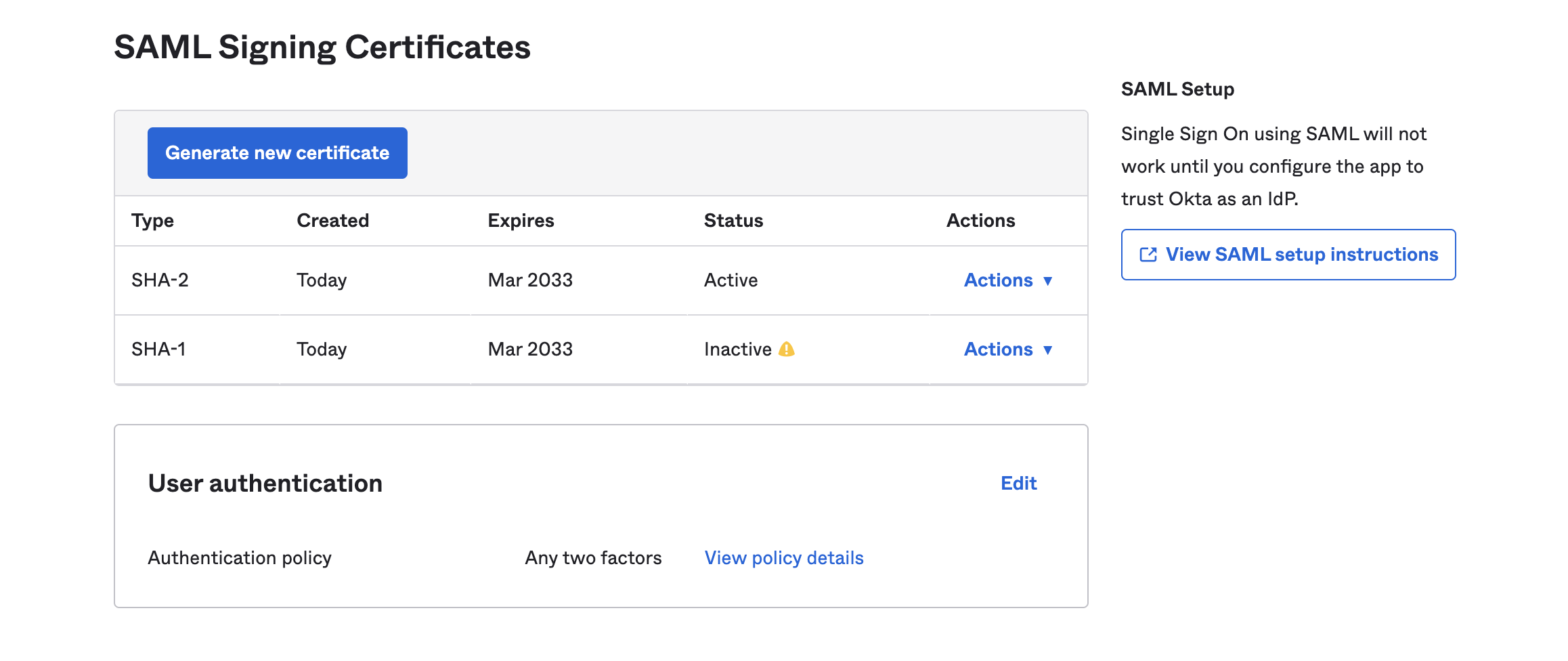
- Click on the
View SAML setup instructionsbutton on theSign Ontab of the application:
GreenOps Helm Configuration
Now we can configure SSO using the Okta SAML template on this page.
-
Take the
Identity Provider Single Sign-On URL(should look like:https://9575730.okta.com/app/9575730_greenops/exa4hxjol7MQjitBz697/sso/saml) and enter it intossoURLofconnector.config. -
Set the
redirectURIofconnector.configas the same callback URL you entered when setting up the Okta application. -
Set
sso.config.urlto be whatever the root GreenOps URL is (example:https://your.greenopsinstance.com). -
Set the
redirectURIof thestaticClientsto behttps://<GREENOPS_URL>/oauth2/callback. -
For
caDatainconnector.config, download theX.509 Certificatefrom Okta. run the file through base64 encoding twice, then create a secret using that value. This is necessary because the Dex configuration requires a base 64 encoded string. Only encoding the certificate once would put the original certificate in the Dex configuration. Run this to get the encoded certificate:base64 -i <CERT_FILENAME> | base64 -i -Create a secret with the output:
apiVersion: v1 kind: Secret metadata: name: sso-info-secret namespace: greenops labels: # This is very important to add. If the part-of label is not added, the secret will not be accessible. app.kubernetes.io/part-of: argocd type: Opaque data: okta-cert: <OUTPUT_OF_PREVIOUS_COMMAND>
The final SSO configuration in the helm chart should look like:
sso:
enabled: true
config:
url: "https://your.greenopsinstance.com"
dex.config: |-
connectors:
- type: saml
id: saml
name: okta
config:
ssoURL: https://9575730.okta.com/app/9575730_greenops/exa4hxjol7MQjitBz697/sso/saml
caData: $sso-info-secret:okta-cert
redirectURI: https://your.greenopsinstance.com/api/dex/callback
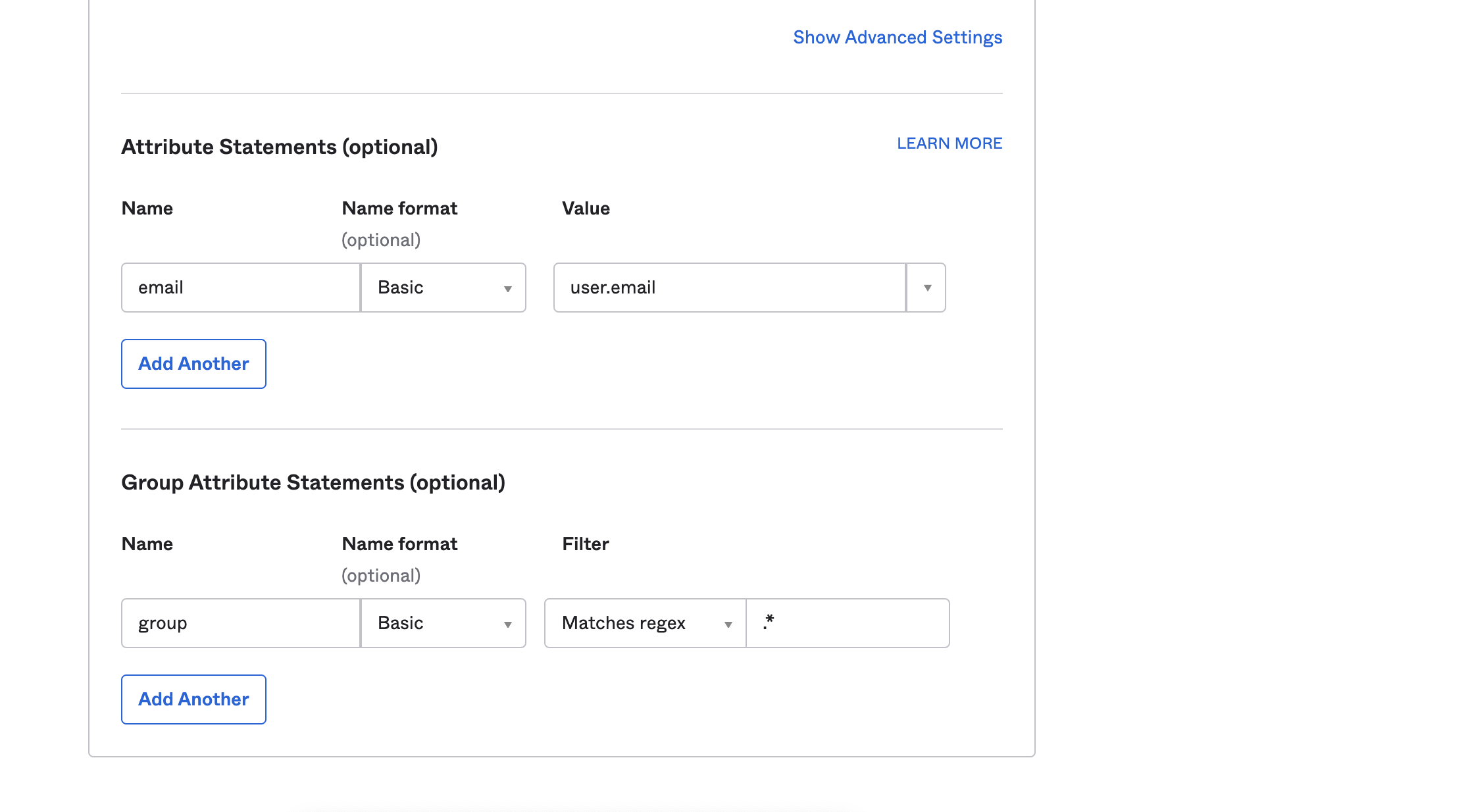
usernameAttr: email
emailAttr: email
groupsAttr: group
staticClients:
- id: greenops-sso
name: GreenOps-SSO
redirectURIs:
- https://your.greenopsinstance.com/oauth2/callback
secretEnv: GREENOPS_SSO_CLIENT_SECRET
Apply this, and you will now be able to use SSO login for Okta!
Note: The application should be configured with users or groups, or no one will be able to login.
Configuring RBAC
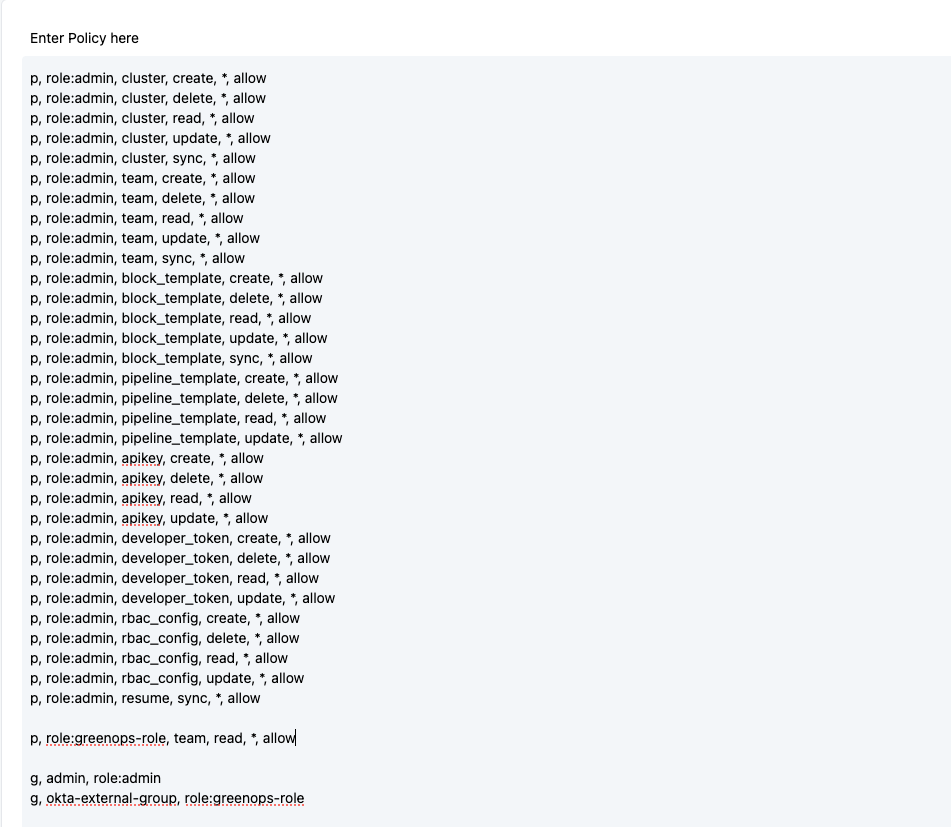
Navigate to the Settings > RBAC section via the GreenOps UI. You should see a policy on the screen that looks like:
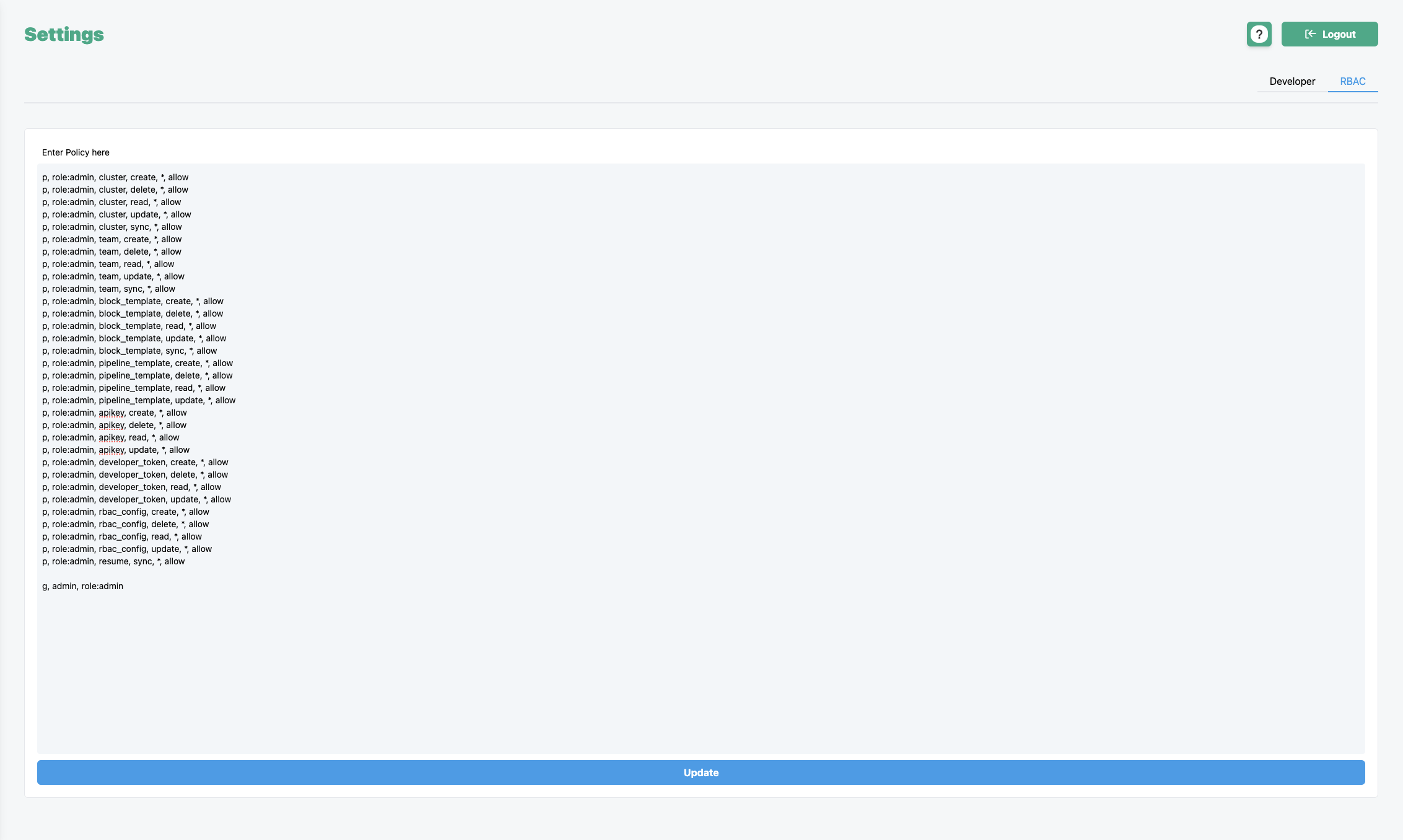
Add your custom groups/roles from Okta into the g section at the bottom of the policy.
For example, you can add a policy like g, okta-external-group, role:greenops-role. The role:greenops-role can be used to define policies for reading pipelines, resuming pipelines, linking clusters, and more. More information on configuring RBAC can be found here. Below is an example configuration that allows Okta users in the group okta-external-group to view all teams, but nothing else: